Private and public officials continue to scramble around the clock to address the Apache Log4j vulnerability since initial reports of the exposed code sent the cybersecurity world into turmoil last Friday.
This article provides an update on the government initiatives aimed at the Apache Log4j vulnerability, recent statistics showing the severity of attack attempts and the possibility of threat actors exploiting the vulnerability for future ransomware attacks.
Government Response to Apache Log4j
As cyber and IT professionals continue to work endlessly to combat the Apache Log4j vulnerability, government officials are joining the fight by developing resources and partnering with industry experts and officials to address what is considered one of the worst security flaws of all time.
Cybersecurity and Infrastructure Security Agency (CISA) Director Jen Easterly held a phone briefing regarding the vulnerability, stressing its severity and scale.
“We expect the vulnerability to be widely exploited by sophisticated actors and we have limited time to take necessary steps in order to reduce the likelihood of damage,” said Easterly. “The issue is an unauthenticated remote execution vulnerability that could allow an intruder to take over an affected device.”
CISA Information Security Specialist Jay Gazlay of the Vulnerability Management Office also commented that he estimates hundreds of millions of devices are now vulnerable to unauthenticated remote execution, which allows intruders to take them over.
CISA has joined several other agencies across the world, including Canada, New Zealand and the United Kingdom (UK), to develop dedicated webpages providing trusted resources for organizations to leverage. The CISA page is at www.cisa.gov/uscert/apache-log4j-vulnerability-guidance and provides real-time updates on the the Log4j vulnerability, including the alert below:
Apache released Log4j version 2.15.0 in a security update to address this vulnerability. However, in order for the vulnerability to be remediated in products and services that use affected versions of Log4j, the maintainers of those products and services must implement this security update. Users should refer to vendors for security updates.
Given the severity of the vulnerability and the likelihood of increased exploitation by sophisticated cyber threat actors, CISA urges vendors and users to take the following actions outlined.
Vendors
- Immediately identify, mitigate, and patch affected products using Log4j
- Inform your end users of products that contain this vulnerability and strongly urge them to prioritize software updates
Affected Organizations
- In addition to the immediate actions—to (1) enumerate external-facing devices that have Log4j, (2) ensure your SOC actions alerts on these devices, and (3) install a WAF with rules that automatically update— review CISA’s upcoming GitHub repository for a list of affected vendor information and apply software updates as soon as they are available. See Actions for Organizations Running Products with Log4j below for additional guidance. Note: CISA has added CVE-2021-44228 to the Known Exploited Vulnerabilities Catalog, which was created according to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities. In accordance with BOD 22-01, federal civilian executive branch agencies must mitigate CVE-2021-44228 by December 24, 2021
Actions for Organizations Running Products with Log4j
CISA recommends affected entities:
- Review Apache’s Log4j Security Vulnerabilities page for additional information and, if appropriate, apply the provided workaround:
- In releases >=2.10, this behavior can be mitigated by setting either the system property
log4j2.formatMsgNoLookupsor the environment variableLOG4J_FORMAT_MSG_NO_LOOKUPStotrue. - For releases from 2.7 through 2.14.1 all
PatternLayoutpatterns can be modified to specify the message converter as%m{nolookups}instead of just%m. - For releases from 2.0-beta9 to 2.7, the only mitigation is to remove the
JndiLookupclass from the classpath:zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class.
- In releases >=2.10, this behavior can be mitigated by setting either the system property
- Apply available patches immediately. See CISA’s GitHub repository for known affected products and patch information.
- Prioritize patching, starting with mission critical systems, internet-facing systems, and networked servers. Then prioritize patching other affected information technology and operational technology assets.
- Until patches are applied, set
log4j2.formatMsgNoLookupstotrueby adding-Dlog4j2.formatMsgNoLookups=Trueto the Java Virtual Machine command for starting your application. Note: this may impact the behavior of a system’s logging if it relies on Lookups for message formatting. Additionally, this mitigation will only work for versions 2.10 and above. - As stated above, BOD 22-01 directs federal civilian agencies to mitigate CVE-2021-44228 by December 24, 2021, as part of the Known Exploited Vulnerabilities Catalog.
- Conduct a security review to determine if there is a security concern or compromise. The log files for any services using affected Log4j versions will contain user-controlled strings.
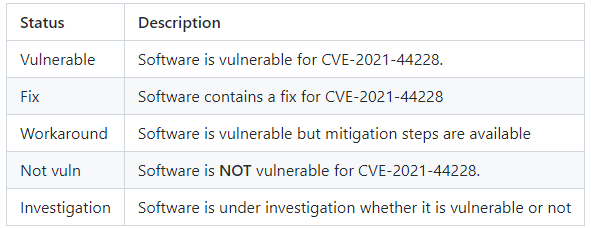
Additionally, the UK National Cyber Security Centre (NCSC) created a sourced A-Z list on GitHub of all known affected software products marked with one of the defined statuses outlined below.
The list is available at https://github.com/NCSC-NL/log4shell/tree/main/software.
Apache Log4j Attack Update
A recent report states that Log4j-related attacks accelerated throughout the past few days and, at points, researchers were witnessing more than 100 attacks per minute. The same report identified Chinese state-backed threat actors as some of the largest perpetrators, launching an estimated 840,000 attacks on companies since last Friday.
So what are attackers after? A large-scale vulnerability such as this provides endless motives for threat actors, including scanning systems to install malware, stealing user credentials and cryptojacking. Reports also confirm several botnets, including Mirai, Tsunami and Kinsing, are attempting to take advantage of the vulnerability.
Additionally, Microsoft has stated they are witnessing activity including credential theft, lateral movement and data exfiltration in a post to their Guidance for preventing, detecting, and hunting for CVE-2021-44228 Log4j 2 exploitation blog.
One positive note coming out of the updates is that there is no evidence of an active supply-chain attack (for now at least).
Unfortunately, the omnipresent nature of the vulnerability means the window for threat actors to gain access remains open. A number of organizations are still unsure if the vulnerability impacted them, and vendors are still scrambling for patches.
While data breaches are nothing new, the scale and scope of this flaw has many cybersecurity professionals extremely concerned. Director of Threat Intelligence and Research for Checkpoint Lotem Finkelstein commented on the potential long-term impact of the situation.
“I cannot overstate the seriousness of this threat. On the face of it, this is aimed at cryptominers, but we believe this creates just the sort of background noise that serious threat actors will try to exploit in order to attack a whole range of high-value targets such as banks, state security and critical infrastructure.”
Apache Log4j and Ransomware
Shortly after the Log4j vulnerability took over the headlines, two major ransomware attacks hit global HR software provider Kronos and the Virginia State Legislature. As of the time this article was written, the timing is simply coincidental, with neither incident reporting connections with the Log4j vulnerability. However, that does not mean threat actors are not strategizing about how to exploit the vulnerability for ransomware attacks.
A large cybersecurity firm stated that they are seeing indicators of attackers exploiting Log4Shell to lay the groundwork for ransomware attacks. Microsoft’s threat intelligence teams also reported they are seeing Log4Shell exploited to install the popular cybercriminal tool Cobalt Strike, which is a regarded as a precursor to deploying ransomware.
Despite the speculation and recorded activity, no ransomware groups have pulled the trigger as of the time this article was written – however, our team will continue to monitor the potential ransomware threat as it develops.
Apache Log4j Government Resources
- Canadian Center for Cyber Security Active Exploitation of Apache Log4j Vulnerability Center
- CISA Apache Log4j Vulnerability Guidance
- New Zealand Log4j RCE 0-Day Actively Exploited Advisories
- NCSC Apache Log4j 2 Vulnerability Alert
This article is a continuation of our Apache Log4j Vulnerability series, available at /our-thoughts-on/category/cybersecurity. We encourage you to share our article with your network and reach out with any questions at [email protected].
Apache Log4j CISA Resources
- CISA Apache Log4j Vulnerability Guidance
- CISA Log4j (CVE-2021-44228) Vulnerability Guidance Github Repository
Apache Log4j Web Resources
- Apache – Log4j Security Vulnerability Center
- GitHub – BlueTeam CheatSheet * Log4Shell*
- Github – Log4j RCE Exploitation Detection
Related Articles
- Apache Log4j Vulnerability Update
- Apache Log4j Vulnerability Update – CISA Issues Emergency Directive
- Apache Log4j Vulnerability Update – Remediation Tools and Patches
About Schneider Downs Cybersecurity
The Schneider Downs cybersecurity practice consists of experts offering a comprehensive set of information technology security services, including penetration testing, intrusion prevention/detection review, ransomware security, vulnerability assessments and a robust digital forensics and incident response team. For more information, visit www.schneiderdowns.com/cybersecurity or contact the team at [email protected].
In addition, our Digital Forensics and Incident Response teams are available 24x7x365 at 1-800-993-8937 if you suspect or are experiencing a network incident of any kind.
Want to be in the know? Subscribe to our bi-weekly newsletter, Focus on Cybersecurity, at www.schneiderdowns.com/subscribe.