What are callback phishing attacks and why are they becoming so popular with threat actors?
Callback phishing attacks, also known as hybrid vishing attacks, have increased 625% from the Q1 2022, according to the recent Quarterly Threats Trends & Intelligence Report from Agari.
The large spike in callback phishing attacks comes after another report that vishing attacks had already increased 550% between the Q1 2021 and Q2 2022. In fact, a UK phone carrier recently reported they block close to one million vishing calls a day.
What is Callback Phishing?
While many of us are trained to report or ignore the typical fraudulent emails that are riddled with typos and malicious links, callback phishing attacks rely on the victim to call them first. These attacks use multi-tiered communications and social engineering tactics to trick the end users into calling a fraudulent number to provide their sensitive information.
How Do Callback Phishing Attacks Work?
The typical callback phishing attack begins by sending the target a phishing email usually under the guise of a subscription or invoice notice that includes a callback number that puts the recipient on the phone with a threat actor who uses social engineering to get sensitive information out of the caller or remote access to their network.
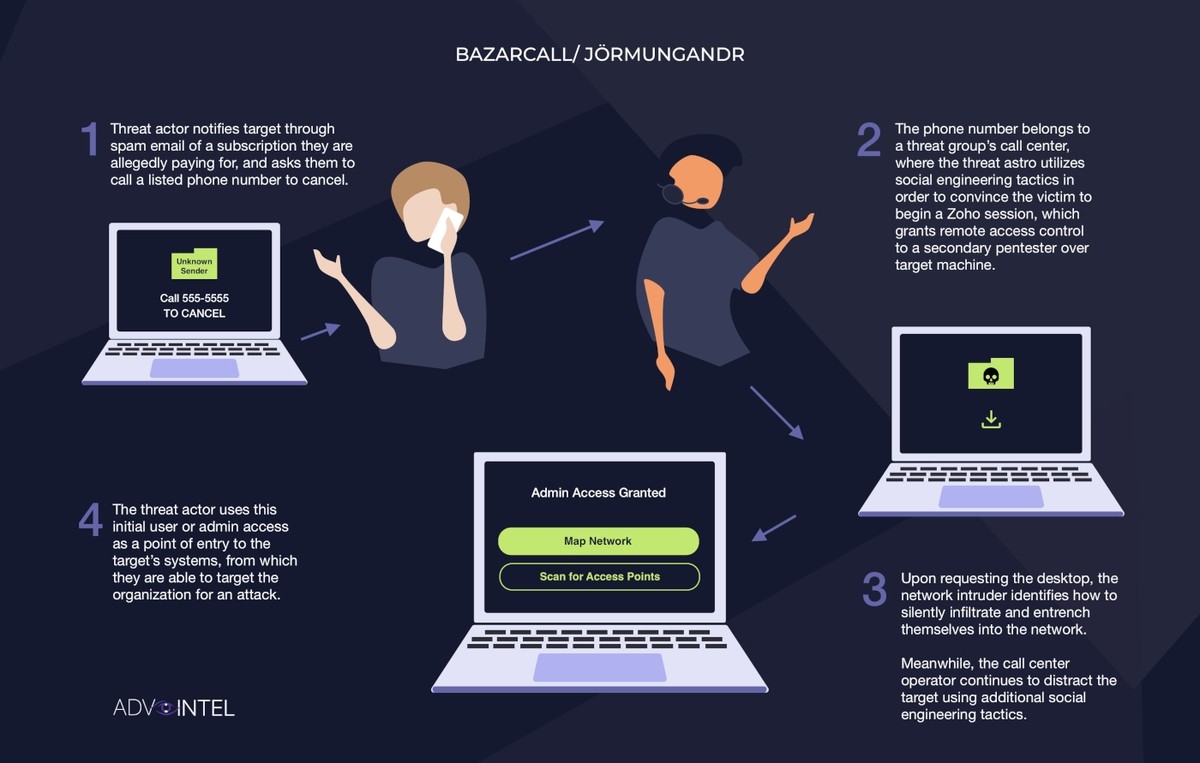
One of the first large-scale callback phishing attacks was the BazarCall campaign perpetrated by the Ryuk ransomware group in March 2021.
Image: www.techrepublic.com/article/bazarcall-attack-increasingly-used-by-ransomware-threat-actors/
The BazarCall campaign started with an email notifying the recipient that a subscription was set for auto-renewal and to call the customer service number to cancel the payment.
Those who called the number were sent to a call center that used social engineering tactics to convince the caller to begin a remote session using legitimate desktop software that gave direct, undetected access into the caller’s network.
Once the session began, the call representative continued to distract the caller on the phone while a network intruder was silently infiltrating the network.
Why are Callback Phishing Campaigns Rapidly Growing?
At this point, many of us are able to quickly identify a phishing email or phone scam pretty easily, and even if some campaigns are designed well, most computers and smart devices have built-in blocking technology that makes it so we don’t even see them. So why are callback phishing campaigns seemingly more effective than the traditional phishing or vishing scam?
First, the phishing emails used are a bit more sophisticated than the standard Nigerian prince scam—the urgency is subtle and provides a callback number versus the traditional “this is super urgent, click here or else” narrative.
Second, many of us have been told that if you are suspicious of an email, you should call the company to verify if the communication is legitimate. By placing a callback number in the body of the phishing email, these campaigns are preying on the instinct to call and talk to a “real” person.
Third, the threat actor picking up the phone may be part of a well-trained call center, specifically trained to be professional and sound legitimate. Remember, many ransomware groups are organized very business-like and know that the longer they keep you on the phone, the more damage they can likely do.
Fourth, the software used for remote sessions contain legitimate tools that are widely used, so when remote sessions open up, the tools usually go undetected by security software.
In fact, this approach is now reportedly being used by three Conti-based ransomware groups who have adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology.
How to Identify and Avoid Callback Phishing Attacks
The best way to avoid becoming a victim of a hybrid vishing campaign is to quickly identify and delete/report the initial email.
While these emails impersonate legitimate companies, they still have several characteristics of phishing emails, such as coming from a public email domain (gmail, outlook, etc.) and containing grammatical errors. Organizations should share the responsibility with the end users by providing adequate cybersecurity training and investing in security software to prevent the emails from even reaching inboxes.
Another identifier is the callback number, which in most cases, the email provides only one number to call despite most companies supplying several numbers to call based on your needs.
We strongly recommend only using verified callback numbers for your accounts—found on the back of financial cards, by safely visiting their website (typing the address, not clicking hyperlinks or googling) or even visiting brick and mortar locations. Think about it, if the email is suspicious, the phone number isn’t any better.
Finally, use common sense, especially when dealing with company systems. If somebody was to knock on your front door and say they were there to fix your HVAC despite the fact you never called anybody, would you let them in?
Same rules apply here. If anybody is requesting remote access, credentials or other sensitive information on the other end of the phone, disengage and contact the appropriate person or department.
If for whatever reason you do provide remote access or notice anything indicating your system has been compromised, immediately disconnect from the internet and contact your IT team.
About Schneider Downs Cybersecurity
The Schneider Downs cybersecurity practice consists of experts offering a comprehensive set of information technology security services, including penetration testing, intrusion prevention/detection review, ransomware security, vulnerability assessments and a robust digital forensics and incident response team. In addition, our Digital Forensics and Incident Response teams are available 24x7x365 at 1-800-993-8937 if you suspect or are experiencing a network incident of any kind.
To learn more, visit our dedicated Cybersecurity page or contact the team at [email protected].
Want to be in the know? Subscribe to our bi-weekly newsletter, Focus on Cybersecurity, at www.schneiderdowns.com/subscribe.
Related Posts
No related posts.