The recent spread of ransomware has kickstarted many companies into reevaluating their current cybersecurity maturity. It has come to be generally accepted that appropriate investment in offline backups will render most ransomware attacks ineffective. The victim may still spend time and money investigating how the infection started, if and what data was exfiltrated, and how to prevent a future incident, but in the end, access to the data is not lost.
Criminals have realized that for their malware campaigns to remain effective in today’s cyber landscape, they must constantly evolve their tactics and techniques. New techniques include a data exfiltration step as part of the ransomware infection. If the ransom is not paid, the attackers threaten to release the victim’s data onto the public internet. While variants of ransomware have made these threats in the past, a new ransomware known as Maze has become the first to actually publish data from alleged victims.
The Origins of Maze
The Fallout exploit kit first appeared for sale in September 2018, with a good deal of interest from the cyber crime community. An exploit kit is a way to automatically and silently exploit a victim’s computer, and is often placed within a compromised website. When a user visits the site, the kit scans for any vulnerable browser-based applications that it can exploit. If the system is patched, it may attempt a social engineering attack on the user. Maze infected its first victim in October of 2019, having been spread by the Fallout exploit kit, hacked RDP connections, and phishing campaigns impersonating government employees.
The original Fallout Exploit Kit thread. There were over 125 replies of interested buyers.
How Maze Works
After gaining access to the machine, the attackers export any data they want and drop the ransomware portable executable on the computer. Following data exfiltration, the ransomware executable first deletes any backups that are stored on the computer and then encrypts all files with the ChaCha algorithm. Finally, it re-encrypts the ChaCha keys with RSA-2048, and appends each file with a random extension. A simple text file named “DECRYPT-FILES.txt” providing instructions for contacting the Maze organization is placed in each of the directories. This sequence of operations renders the data impossible to decrypt without paying the attacker.
Minutes after the portable executable runs, the user’s desktop background is changed with an explanation of what happened.
The ransom note that is dropped in all the user directories.
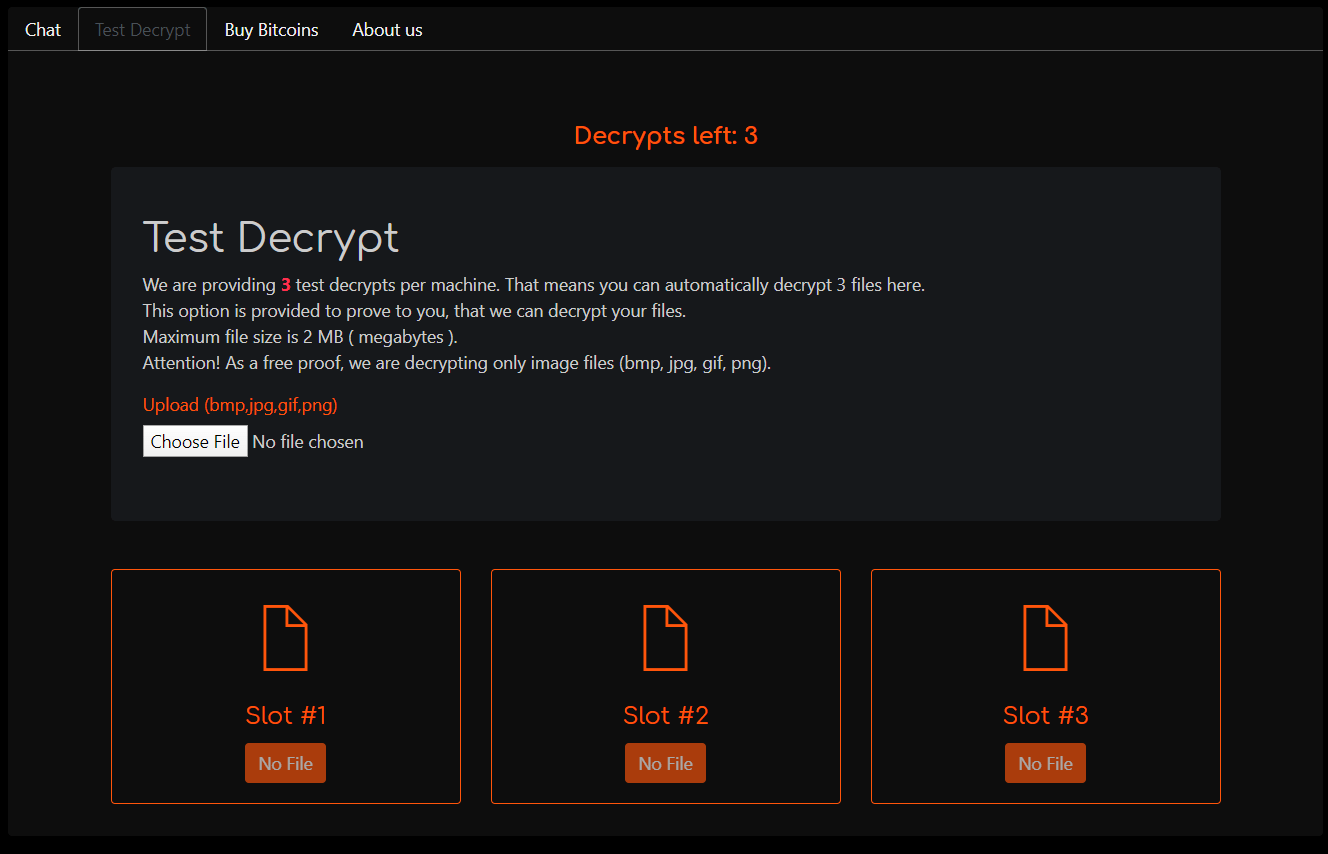
Each user is given a url with a unique path that corresponds to the victim. The website contains five different tabs.
A live chat to negotiate with the criminals.
The site allows for three image files to be decrypted.
Exchanges where the victim can purchase bitcoins.
Links to news articles about the ransomware.
Impact of Maze
Maze is unique in following through with the public announcement of companies that have not paid the ransom. As of Janurary 27, more than twenty five companies have been named as not paying. The operators of Maze have also listed the date the ransomware attack occured, IPs/names of the locked computers, and several files for proof such as revenue statements, account balances, service agreements, etc. None of the ten companies have made a public statement declaring a breach.
The Maze shaming website.
Schneider Downs recommends that all organizations doing business with any of the listed companies perform a risk assessment to determine if the breach could impact their own operations.
A proof file containing a list of deposits.
Nondisclosure of a data breach involving personally identifiable information (PII) can result in lawsuits, fines, and even jail time for American companies and their Boards. For countries that fall under GDPR, fines can exceed 20 million Euros. Although pay the ransom may reduce the likelihood of Maze releasing stolen data publicly, most privacy regulations still require organizations disclose the breach of PII by a criminal organization. There is currently no indication that Maze has stolen PII from any of its alleged victims.
Detecting Maze
The following indicators of compromise (IOCs) can be used to detect activity related to the precense of Maze malware.
File Characteristics:
- SHA256 – 91514e6be3f581a77daa79e2a4905dcbdf6bdcc32ee0f713599a94d453a26fc1
- SHA1 – 49cdc85728bf604a50f838f7ae941977852cc7a2
- MD5 – 8205a1106ae91d0b0705992d61e84ab2
Connections (All Russian Servers):
- 91.218.114.4
- 91.218.114.26
- 91.218.114.11
- 91.218.114.31
- 91.218.114.25
- 91.218.114.37
- 91.218.114.32
- 91.218.114.38
- 91.218.114.79
- 91.218.114.77
Registry Edits:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftTracing1473359_RASMANCS
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftTracing1473359_RASAPI32
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet SettingsConnections
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet SettingsZoneMap
- HKEY_CURRENT_USERSoftwareMicrosoftSpeechCurrentUserLexicon
- HKEY_CURRENT_USERSoftwareMicrosoftSpeechPhoneConverters
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionShell ExtensionsCached
- HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionTaskManager
How Can Schneider Downs Help?
The Schneider Downs cybersecurity practice consists of experts in multiple technical domains. We’re an authorized reseller of both Mimecast® and Carbon Black and offer comprehensive Digital Forensics and Incident Response services. For more information, visit www.schneiderdowns.com/cybersecurity or contact us at [email protected].