The ambiguity around Twitter’s verification system has become a cybersecurity concern as threat actors are using the uncertainty to fuel a recent round of phishing emails.
The month-long “will he or won’t he” saga surrounding Elon Musk’s purchase of Twitter effectively came to an end on October 28th when he officially acquired the social media platform for approximately $44 billion.
One of the first Twitter features Musk indicated he would change is the verification process. Since Twitter’s inception, the platform has offered a “verified badge,” which is a small blue check mark on accounts to notable users, including politicians, organizations, journalists, athletes and other public figures.
Being “verified” has been an important feature for the social platform where spambots and ill-intentioned people can easily create a fake account imitating a news source or public figure. If you are an avid Twitter user, you most likely use the blue check mark to validate the source of content—something especially important in the environment over the past few years.
After officially taking over, Musk made clear his plan to change the verification process, suggesting a paid subscription for every user as part of the existing Twitter Blue premium subscription. He initially considered a $19.99 monthly fee, but following backlash, recently suggested an $8 package that includes less advertisements, priority interactions and extended media capabilities in addition to the verified badge. However, it is important to note nothing is official as of the timing of this article.
This, of course, has set off many users who were already opposed to Musk owning Twitter—those who were vocal in their opposition of a paid requirement of any kind, citing the danger of verifying anybody who wants to be and in turn, making it extremely difficult to trust information.
This debate about a new paid verification process has become a popular headline, which in turn, has gained the attention of threat actors who wasted no time getting involved.
There have been several reports circulating with regard to a new phishing campaign that attempts to obtain account usernames and passwords from existing users under the guise of a Twitter help form. The email targets existing verified accounts, requesting users provide account information to keep the free verified status before the $19.99 a month fee starts on November 2, 2022.
As with most phishing campaigns, there are obvious warning signs the email is fraudulent. The sender email address is “[email protected]”, the subject line is “RE: Twitter Warning” and there is a soft sense of urgency with the narrative.
It is also important to note that, unlike many phishing campaigns, there is no request for financial information and those who are managing social media for businesses or public figures may use poor judgement and just chalk up the request as part of the “new” Twitter verification process.
This phishing campaign was built through several Google apps that may have helped it bypass Google’s automatic scanning tools and included an embedded Russian web host. The campaign was eventually taken down, but is likely just the first of many campaigns trying to capitalize on both rumored and real changes to Twitter under its new ownership.
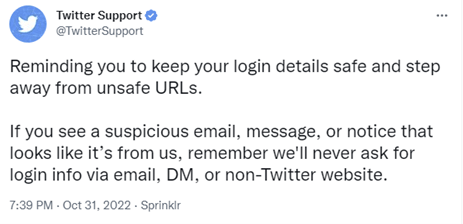
Twitter is aware of the recent phishing campaign and has tweeted a reminder from @TwitterSupport reminding users that they will never solicit users for login information via email, DM or non-Twitter websites.
Regardless, the fact that we rely on the verified badge on the Twitter Support account to trust the information is ironic given the topic of the article.
The new Twitter model should be an interesting experience at the very least.
About Schneider Downs Cybersecurity
The Schneider Downs cybersecurity practice consists of expert practitioners offering a comprehensive set of information technology security services, including penetration testing, intrusion prevention/detection review, ransomware security, vulnerability assessments and a robust digital forensics and incident response team. In addition, our Digital Forensics and Incident Response teams are available 24x7x365 at 1-800-993-8937 if you suspect or are experiencing a network incident of any kind.
To learn more, visit our dedicated Cybersecurity page or contact the team at [email protected].
Want to be in the know? Subscribe to our bi-weekly newsletter, Focus on Cybersecurity.
Related Posts
No related posts.