What are the key differences between identity theft and identity fraud?
Did you know that identity theft is three times higher in the U.S. than in other countries? In fact, recent reports indicate that nearly 33% of Americans have experienced some kind of identity theft attempt in their lives. Many experts agree that this number will increase significantly in the coming years.
In the first article of a series dedicated to navigating the identity fraud landscape through effective detection, prevention and correction efforts, we discuss the basics when it comes to identity theft and fraud.
Protecting yourself from identity theft and fraud starts with familiarizing yourself with key definitions and examples. According to Javelin Strategy & Research, identity theft and identity fraud are sometimes used interchangeably, but they are, in fact, different.
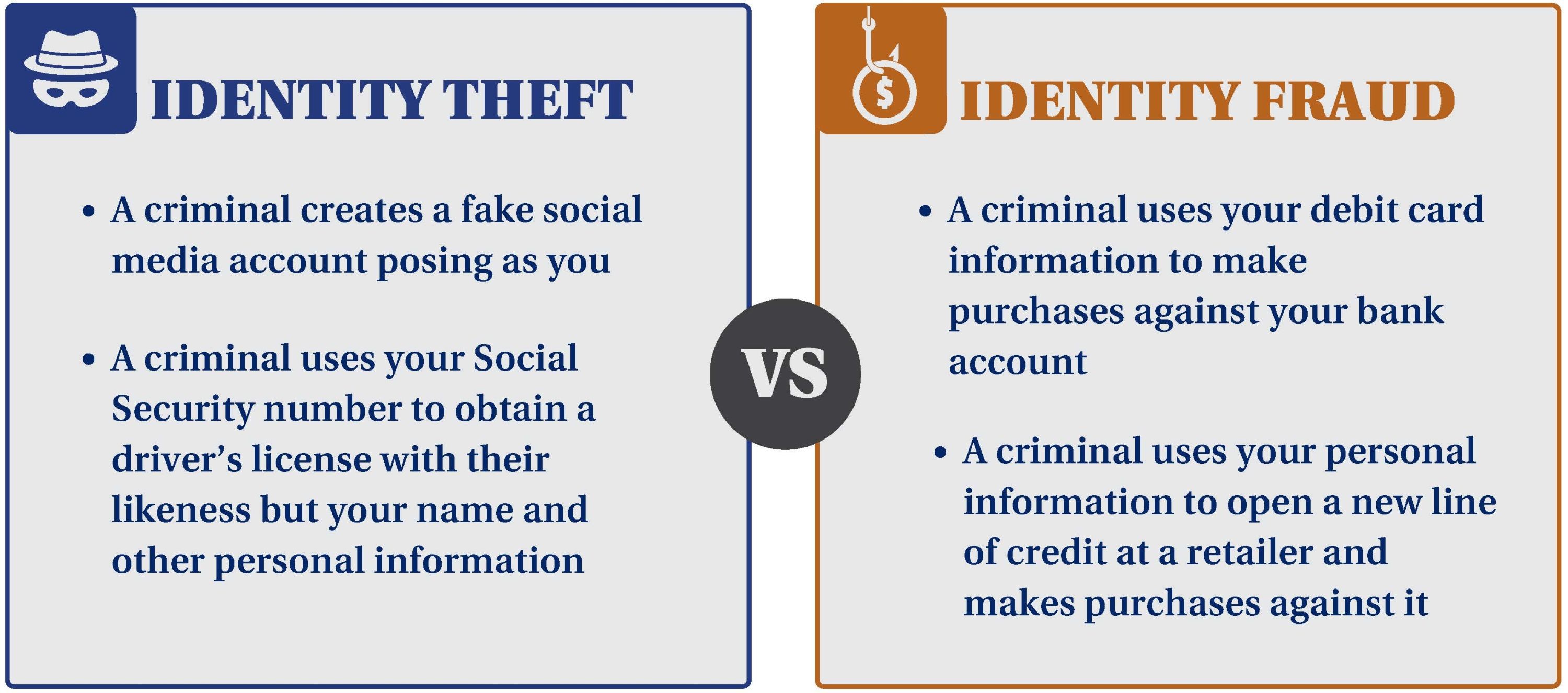
Identity Theft vs. Identity Fraud
Identity theft is when unauthorized access of your personal information occurs. There are also Special Forms of Identity Theft that the FTC recognizes such as Tax, Child and Medical Identity Theft. Tax Identity Theft is when someone uses your Social Security number to get a tax refund. Child Identity Theft is when someone uses your child’s information to commit fraud. Medical Identity Theft is when someone uses your information to get medical services and/or get copies of your medical records.
Identity fraud goes a step further when threat actors use their unauthorized access of your personal information for illicit financial gain. Criminals use individual identities to create false applications for loans and credit cards, process fraudulent withdrawals from bank accounts, conduct fraudulent use of telephone calling cards or online accounts, or obtain other goods or privileges that the criminal might be denied if they were to use their real name.
Identity theft can occur without identity fraud; for example, a fake dating profile posing as you. But identity fraud can’t occur without identity theft, i.e., opening a new credit card in your name after gaining access to your personally identifiable information. Other key examples are outlined below:
While identity theft and identity fraud are both undesirable, it’s important to distinguish one from the other and be aware of the different methods criminals will use to exploit your personal information.
This is the first article of a series dedicated to navigating the identity fraud landscape through effective detection, prevention and correction efforts. View the other articles here:
- Top 5 Identity Fraud Schemes of 2023
- Prevention and Detection – Key Methods to Protect Against Identity Fraud
How Can Schneider Downs Help?
The Schneider Downs IT Risk Advisory Team can advise you on how to strengthen your organization’s risk management position to ensure optimal asset protection, now and in the future. Feel free to reach out to our team directly at [email protected].
About Schneider Downs IT Risk Advisory
Schneider Downs’ team of experienced risk advisory professionals focuses on collaborating with your organization to identify and effectively mitigate risks. Our goal is to understand not only the risks related to potential loss to the organization but to drive solutions that add value to your organization and advise on opportunities to ensure minimal disruption to your business.
To learn more, visit our dedicated IT Risk Advisory page.