Why are malware-laced fake browser updates having a moment in 2023?
The adage “what’s old is new again,” is certainly true in the cyber threat landscape, and recent reports indicate that one of the oldest malware tricks in the books, fake browser updates, is making a major comeback.
The fake browser update is a simple, yet complex malware attack due to the fact it requires the use of a legitimate website to host malicious JavaScript code.
So, how do legitimate websites get infected? In most cases, threat actors can inject malicious code by finding unpatched vulnerabilities or WordPress misconfigurations–but they can also find their way in through almost any asset hosted on a website, even from third-parties such as media players or templates.
Once installed, the malicious code, hand-in-hand with the website and the campaign, turns its attention to the end user. The job is simple: refer website visitors to the malware by prompting them to update their browsers.
The moment a visitor lands on an infected page, the code starts to run. If the target is a good match, the code will open a new page prompting the end user to update their web browser. In reality, the “update” just downloads malware onto the user’s machine.
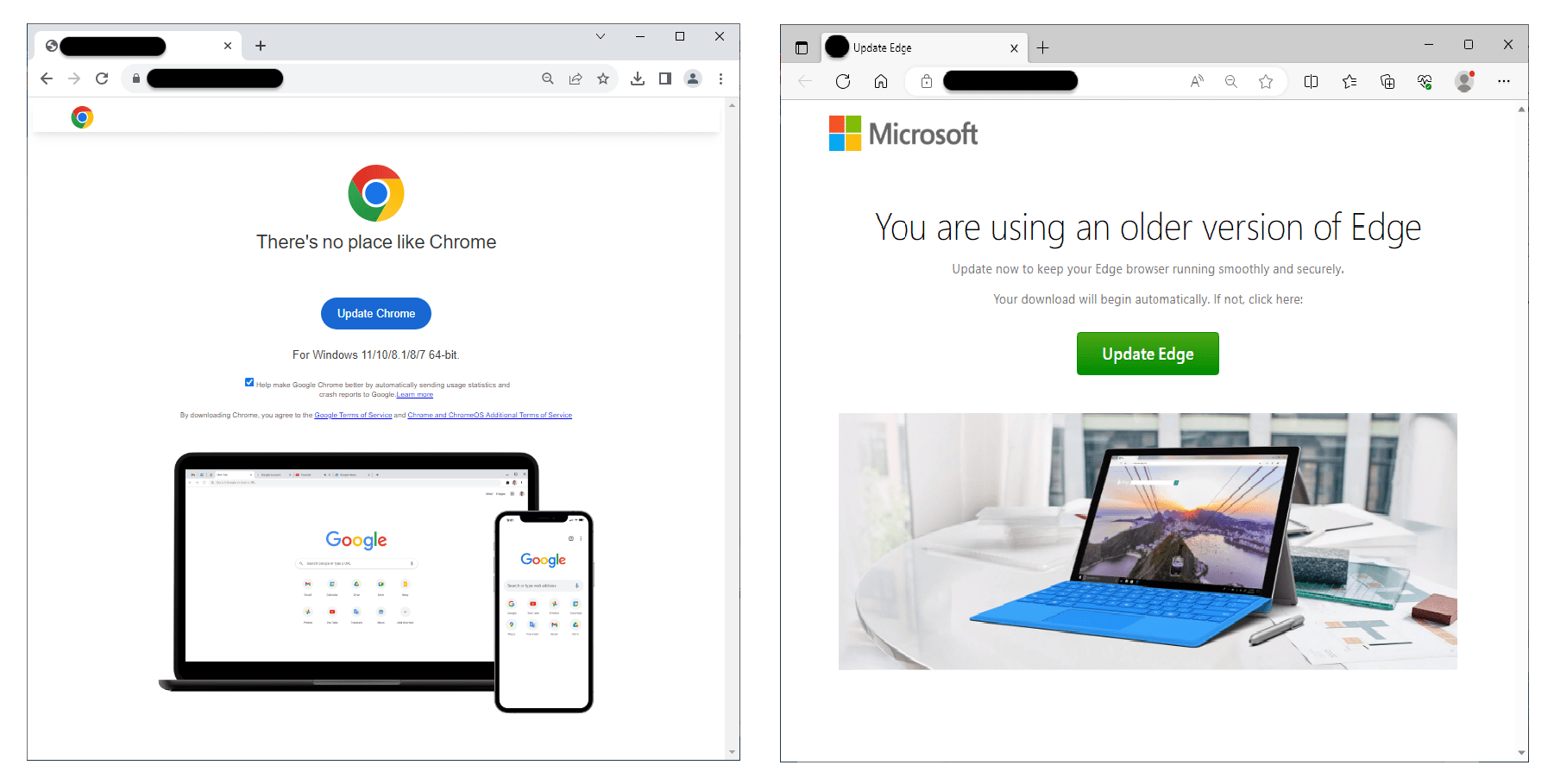
While phishing emails and fraudulent websites are increasingly easy to spot, these malicious update pages can be extremely realistic, as shown in the screenshots below.
Screenshots courtesy of Jerome Segura
Why Are Fake Browser Updates Coming Back?
Krebs on Security reports that these attacks are back on the rise because of a new technique making them harder to stop. The report believes law enforcement and security experts are unable to flag the attacks due to threat actors hosting the malicious files on a decentralized, anonymous cryptocurrency blockchain.
Why Do Fake Browser Update Attacks Work?
These attacks are simple, but effective for a number of reasons. First, these attacks originate from a trusted channel. These aren’t a random link from an unsolicited email or text, these are pages that flip over from real websites. Inherent end user trust is already more established than in the standard phishing attack.
Second, think about one of the most common pieces of cybersecurity advice we receive (and should be following): update your software. In fact, updating software is so important to cyber hygiene that CISA highlighted it as one of the four steps in this years’ Cybersecurity Awareness Month campaign.
In many instances, software updates are automatic, which could be because your IT department set your laptop to restart on a specified cadence or because you selected an automatic update option when configuring software.
With these circumstances in mind, think about what you would do if you were reading a news article on a website you visit daily and you receive a prompt to update your browser… chances are you would follow what you have been trained to do and click update.
How Can You Avoid Fake Browser Updates?
The easiest way to avoid fake browser updates is a little more complicated since these attacks are harder to spot than most others in the wild.
One suggestion is simply letting browsers take care of themselves. In fact, most modern web browsers automatically update in the background, so if you get a prompt to update your browser, it’s safer to simply close the window and move on.
Another option is going through the browsers themselves to verify if any updates are needed. Those using Chrome on Windows OS can do so by:
- Click the Settings icon (three vertical dots) in the top-right corner of the Chrome browser window
- Select Settings from the drop-down menu
- Click About Chrome in the left-hand menu that appears
- This will confirm if Chrome is up to date and, if there is a new version of the browser available, you can securely download and install it here.
If you are a Microsoft Edge or Firefox browser user, links to trusted instructions to verify/update the browsers are below:
Remember: updating your software is important, but so is verifying the source of the request. If you have any questions about update prompts or versioning, please reach out to your IT department or a security professional.
About Schneider Downs Cybersecurity
The Schneider Downs cybersecurity practice consists of experts offering a comprehensive set of information technology security services, including penetration testing, intrusion prevention/detection review, ransomware security, vulnerability assessments and a robust digital forensics and incident response team. In addition, our Digital Forensics and Incident Response teams are available 24x7x365 at 1-800-993-8937 if you suspect or are experiencing a network incident of any kind.
To learn more, visit our dedicated Cybersecurity page or contact the team at [email protected].
Want to be in the know? Subscribe to our bi-weekly newsletter, Focus on Cybersecurity.